- City Fajr Shuruq Duhr Asr Magrib Isha
- Dubai 04:27 05:45 12:20 15:47 18:49 20:07

Number of mobile banking Trojans this year was nine times greater than in the previous year. (YouTube)
The year 2014 has been a watershed year as far as mobile malware is concerned. The number of mobile malicious programs increased by a massive 250 per cent compared to 2013 while the number of banking related Trojans alone went up by a massive 900 per cent.
This was revealed by Kaspersky Lab in its latest report covering cyber threats in 2014.
According to security experts who analysed the data, a total of 6.2 billion malicious attacks on user computers and mobile devices were blocked by Kaspersky Lab antivirus products in 2014, one billion more than in 2013.
“2011 was the year of mobile malware formation, especially on Android-based devices; 2012 was when they developed and 2013 was when they reached maturity. In 2014, mobile malware focused on financial issues: the number of mobile banking Trojans was nine times greater than in the previous year and developing in this area is continuing at an alarming rate,” said Roman Unuchek, Senior Mobile Malware Analyst at Kaspersky Lab.
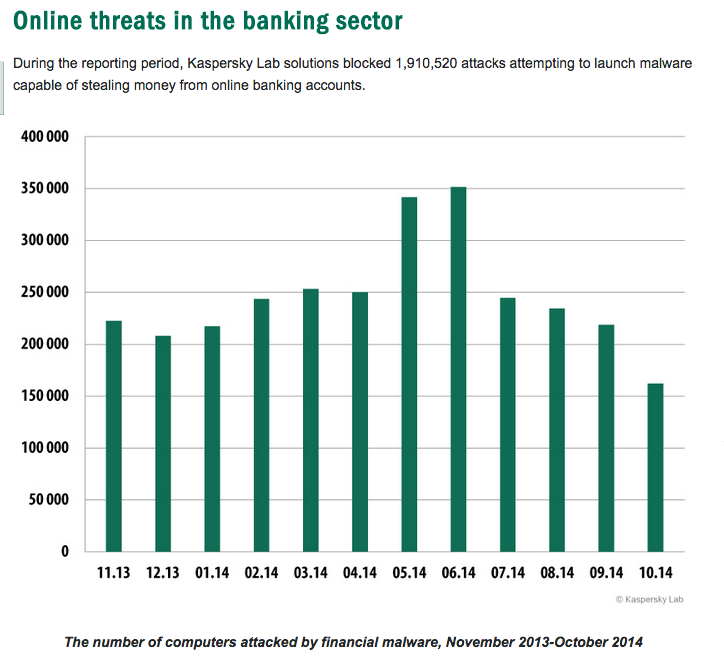
Kaspersky Lab said its solutions had blocked 1.9 million attacks attempting to launch malware capable of stealing money from online banking accounts.
The month of May and June registered the largest numbers of financial attacks. “This might have been caused by an increase in online banking activity at the beginning of the holiday season as well as by the main sport event of the year – the World Cup-2014 in Brazil – where cybercriminals used financial malware to steal tourists' payment data,” the report said.
The year saw a total of 295,500 new mobile malicious programs, 12,100 mobile banking Trojans. Of this about 53 per cent of attacks involved mobile Trojans targeting users’ money while 19 per cent of Android users (one in five) encountered a mobile threat at least once over the year.
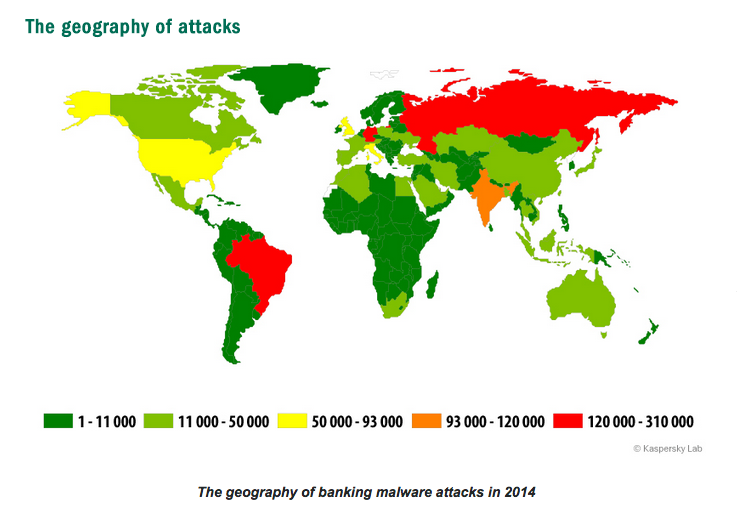
United States continued to remain as the number one destination for malware hosting followed by a new entrant – Germany which replaced Russia for the second spot. The Netherlands remained in 3rd place.
However Russia had the most number of affected users, totalling a massive 45.7 per cent, followed by India at 6.8 per cent.
Vietnam remained the number one in terms of countries with risk of local infection – malicious programs located on users’ computers or on removable media connected to the computers, such as flash drives, camera and phone memory cards, or external hard drives. Vietnam was followed by Mangolia, Bangladesh and Nepal.
Giving more details of the nature of attacks Kaspersky lab said it had blocked attempts to steal money via online access to bank accounts on almost 2 million user computers.
What’s interesting is the number of Mac machines that were targeted. “A total of 3.7 million attempts to infect OS X- based computers were blocked,” the report said. An average Mac user encountered about 9 threats during the year it added.
There was a 400 per cent increase in the number of attacks (1.4 million) Kaspersky Lab blocked on Android devices.
According to the report, fraudsters who target mobile devices with financial malware could be inspired by their experienced “colleagues” who have been stealing money via personal computers for years.
“Zeus remains the most widespread banking Trojan with ChePro and Lohmys coming second and third. Three quarters of attacks targeting users’ money were carried out using banking malware but these are not the only financial threats. Bitcoin wallet theft was the second most popular banking threat (14 per cent). Bitcoin mining software (10 per cent) is another threat related to the crypto currency. It uses computing resources to generate bitcoins,” the report adds.
Maria Garnaeva, Security Expert at Kaspersky Lab’s Global Research and Analysis Team, said: “One of the most effective ways to deliver malware to user computers is to exploit vulnerabilities in Oracle Java and in browsers such as Explorer, Mozilla Firefox, etc. In addition, cybercriminals continue to use exploits for Adobe Reader vulnerabilities. These infection techniques remain popular simply because social engineering techniques are still effective.”
![]() Follow Emirates 24|7 on Google News.
Follow Emirates 24|7 on Google News.